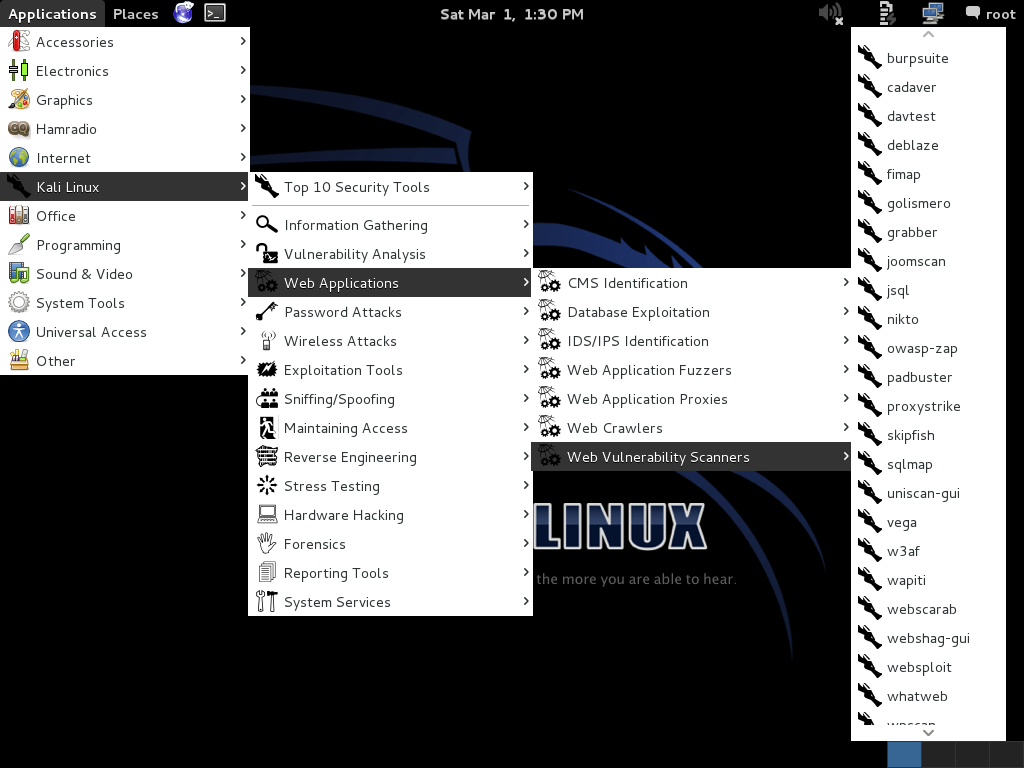
Kali Linux (http://www.kali.org) is a collection of free penetration testing and security auditing tools, all packaged into a single Linux distribution.
- Accompanying slides: Web Security Testing with Kali Linux
Update: An updated version “Web Application Security Testing: Kali Linux Is the Way to Go” was presented at Better Software West 2014 and includes more examples and screen shots of the tools.
Kali Linux contains 300+ tools designed for:
- Information Gathering
- Vulnerability Analysis
- Web Applications
- Password Attacks
- Wireless Attacks
- Exploitation
- Sniffing/Spoofing
- Maintaining Access
- Reverse Engineering
- Stress Testing
- Hardware Hacking
- Forensics
- Reporting
While its primary audience is professional penetration testers, it provides the tools for performing password recovery, forensic analysis, and web application testing. Because the tools are preinstalled, maintained and updated, and configured to work together where appropriate, it is an ideal situation for people and organizations that need to do security testing without having the time and resources to maintain their own custom infrastructure. That said, even organizations that have the time and resources may find that they have little need to maintain a custom infrastructure with Kali Linux available.
For professional penetration testers, Kali Linux includes password crackers, wireless sniffers, network scanners, and explication tools. For forensic analysis, Kali Linux provides a mode that does not touch the internal hard drive, does not auto mount any removable media, and allows a potentially compromised system to be examined in great detail, along with tools to track the information gathered. For IT departments, Kali Linux has network scanners, vulnerability analysis frameworks, and password recovery tools.
Even if you don’t fit into any of those groups, Kali Linux can still be very useful. With the huge number of tools installed, Kali Linux becomes a very nice tool catalog where users can look through a categorized menu of security tools, making it easy to search for a tool that might meet their needs. And since they are preinstalled, the tools can be quickly evaluated. Many of the tools are text-based and run from the command-line, while others have graphical front ends to make them easier to use. Some provide data intended to be fed into other tools, while others provide detailed reporting and management capabilities.
The successor to BackTrack Linux, Kali Linux was released at the end of 2012. It is built on top of Debian Linux, and is distributed in a number different ways. You can download an ISO for installing from scratch, dual booting with Windows, live USB installs, and hard disk installs. VMware images are available for bringing up virtual machines quickly. There is an AMI available for Amazon EC2. Kali can be installed on i386 or x86_64 processors, as well as a whole host of ARM devices such as Raspberry Pi, HP and Samsung Chromebooks, and even the Galaxy Note tablet.
All of this is designed to make it very easy to start using any of the hundreds of security and pen testing tools that are part of the Kali Linux distribution.
The Kali Linux is not a general use Linux distribution. It’s designed to be single user, with the default user of root. It is not recommended for Linux beginners. For starters, because you’re running as root it is easy to make a mess of your system if you aren’t careful. Even more so, the pen testing and security tools included making it easy to unintentionally attack your own organization from within unless you’re very careful.
Here is a quick overview of some of the tools that might be useful for application developers and testers.
Network Scanners
Network scanners can be used to discover hosts on the network, find out what ports and services might be open were exposed on a host, to fingerprint operating systems, and to identify versions of services that are running.
- Nmap
- zenmap
Web Vulnerability Scanners
Web vulnerability scanners have some different flavors. Web server scanners examine web server software, such as Apache, looking for misconfigurations. Web application scanners look at the applications themselves, sometimes focusing on a particular types of vulnerabilities such as cross site scripting (XSS) or SQL injection (SQLi) vulnerabilities.
- Nikto2
- Wapiti
- skipfish
Intercepting Proxies
Intercepting proxies act as a “man-in-the-middle” inspecting requests and responses as they travel to and fro, allowing them to be analyzed or even modified in flight.
- OWASP Zed Attack Proxy
Exploitation Tools
Exploitation tools are usually not used to find vulnerabilities but rather just to exploit them clearly they could be used as true hacker tools but they can also be used to prove that particular vulnerabilities are real and exploitable.
- Metasploit
- Armitage
Vulnerability Management
A vulnerability management systems are used to audit systems, track vulnerabilities, and differentiate new findings and false positives. Many of them are not good one-time scan tools, but rather are complete management systems intended to maintain entire networks over time.
- OpenVAS
- Greenbone Security Desktop/Assistant
Summary
Kali Linux makes a large number security tools easy to find, easy-to-use, and easy to maintain, for security professionals and nonprofessionals like. Just about any development or test group can benefit from spending some time learning to use Kali Linux within their organization.
Broken Web Applications Project
As an aside, if you’re going to start playing around with Kali Linux a good companion is the OWASP Broken Web Applications Project. It provides a virtual machine that runs a variety of applications with known vulnerabilities, which makes it easy to try a lot of the security tools against.
Web Application Security Testing: Kali Linux Is the Way to Go
Gene Gotimer will be discussing and demonstrating Kali Linux and some of the included tools at the Better Software West conference in Las Vegas in June 2014.