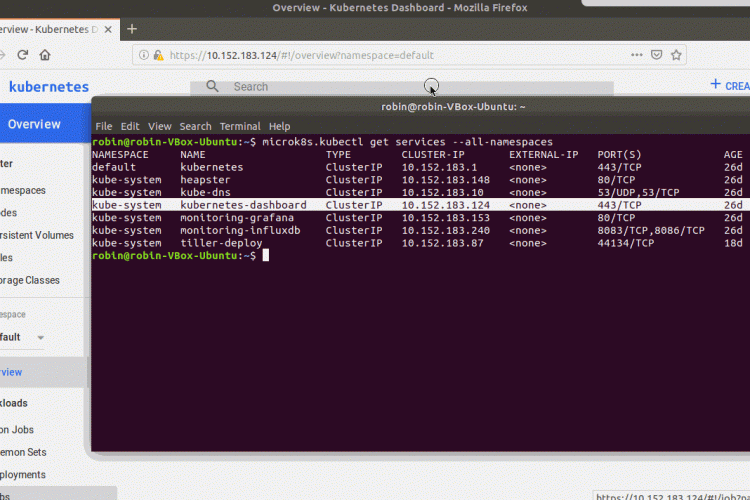
In a recent development, MicroK8s replaced its dockerd installation with containerd. Many pre-existing sources mention “microk8s.docker”, but this command is no longer available. I will walk you through the full initial installation and basic usage on Ubuntu 18.04. Practically speaking, this means you now need to install Docker on your Ubuntu machine. In previous versions, […]
Blog
Insight and analysis from thought leaders in agile development and testing, DevOps, security, test automation, and more.