Dear Loyal Readers,
Security, like safety, almost always makes your life harder. It is inefficient. Now, as I said before, I love Jenkins for scripting and organizing project operations and today I’d like to talk about a security feature that can help you have your cake and eat it too.
The challenge for us is that Jenkins must function, while not revealing to anyone but a select few exactly how it accomplishes its missions. That is, I want to authorize someone to click the button, but not get the root password from the console output.
Enter the credentials binding plugin:
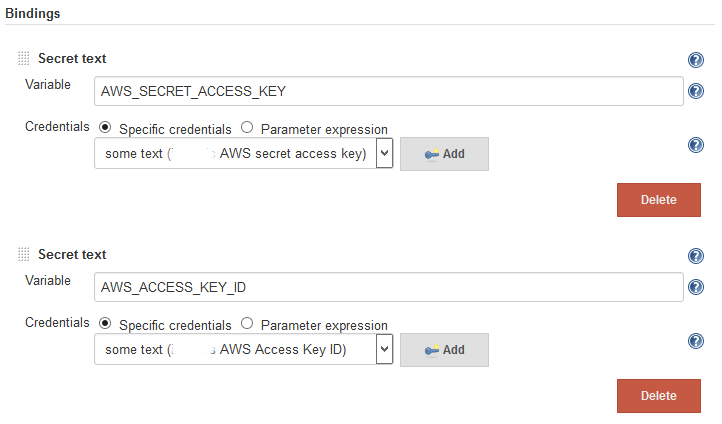
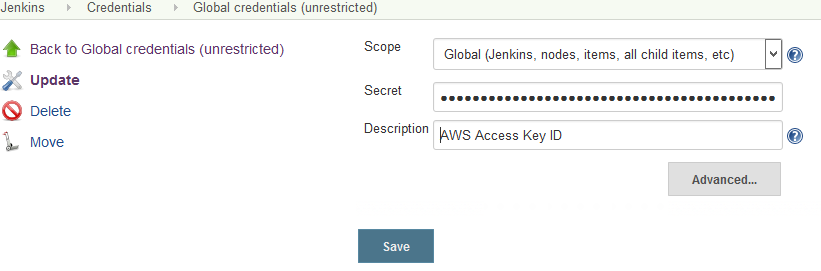
This plugin lets you map secrets to environment variables or secret files to a path available via environment variable. For using AWS we’ll make two secret, one for the Access Key ID, and one for the Secret Access Key.
Finally, we can directly map these secrets to the standard AWS sdk environment variables.
And there it is! Simple, and secure; what more can one ask for?
BONUS TIP
You can silence Jenkins echoing (which sometimes might write secret things to the console output like this:
set +x
echo “About to execute ./set_password -u my_user -p ******”
./set_password -u my_user -p $PASSWORD
set -x